
Beginner Read Digital Strategy
An effective digital strategy can be vital to your organisation’s success. Read on to understand the key considerations when developing yours.
In this article
Cyber security is a critical, yet often overlooked, aspect of your strategy. Understanding what your organisation can do to protect your online and off-line systems and networks will help protect your data from theft and damage. In this article we’ll explore:
Cyber security protects you and your data from digital attacks by safeguarding the networks and devices you use.
Why is understanding cyber security important?
Generally, when using computers and browsing the internet, we all collect, and store highly sensitive data and this data can be exploited and even stolen by criminals.
In this article, you’ll learn the basics of keeping your digital information safe, the types of cybercrime you might encounter and practices you can adopt to better protect your data online.
The three most common types of cyber-attacks are:
What are the risks of cyber-crime?
Failure to put adequate safety measures in place can result in some harmful outcomes.
Phishing is the act of impersonating a person or entity that the victim trusts to gain access to sensitive or personal information. In general, phishing tactics aim to trick users into performing specific actions while online, such as:
How can you spot a phishing email?
Knowing how to spot a fraudulent email is an essential first step to avoid getting phished. The sample email below highlights the most common characteristics of phishing emails:
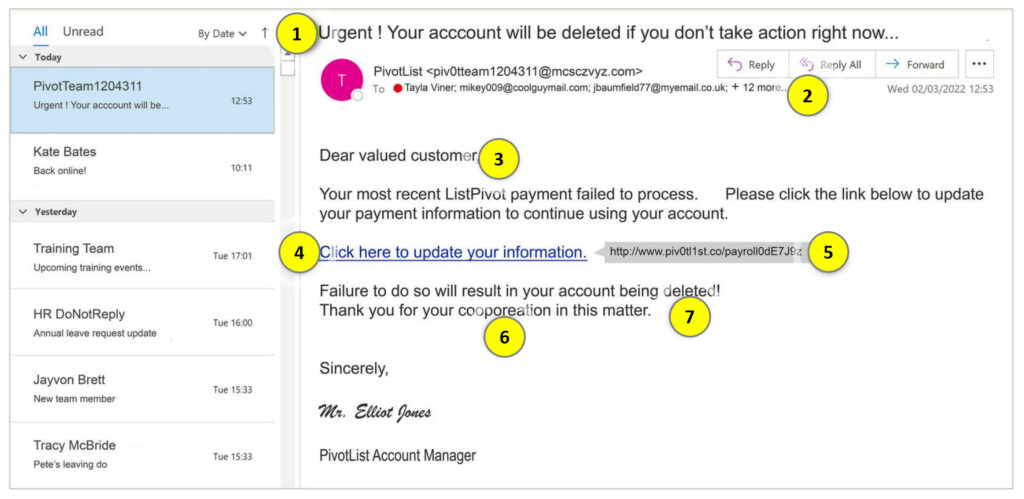
Phishing attacks rely on unsuspecting users clicking without thinking. To avoid becoming the next victim of a phishing scam, here are some simple pointers to help you avoid typical phishing tactics:
Malware is a combination of the words – malicious and software. Criminals use malware to exploit devices to access information, damage programs, or steal personal data for financial gain. Malware doesn’t just impact individuals. An employee who unwittingly installs malware on a company owned device can put their entire organisation at risk. Malware is most often downloaded when an unsuspecting user clicks on a malicious link, file, or attachment.
Below are examples of three types of malware and what they can do:
How you can prevent malware attacks
There are many kinds of malware and malware attacks can have serious implications. Here are a few tips for reducing the risk of exposure to malware:
Can you trust this link?
Messages from seemingly reputable sources can be exploited to send malware to unsuspecting recipients. If tricked into clicking a malicious link, you could become a victim.
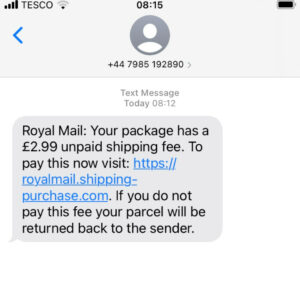
How to minimise the damage of malware
If you have accidentally downloaded malware, here are some tips for how to minimise the damage.
Passwords are the first line of defence against fraud and identity theft. They protect our devices, online accounts, and personal information from unauthorised access.
Many of us still use weak passwords, or worse, the same passwords across multiple accounts. By doing so, we are increasing the risk of getting hacked by cyber criminals – all in the name of convenience. Luckily, there are simple steps you can take to strengthen your password security.
Next time you create a password, use these password tips to make it easy to remember and difficult to hack. If your existing passwords don’t meet the criteria for strong passwords, think about changing them. And remember, never reveal, or share your password with others!
What is multi-factor authentication (MFA)?
MFA is a method of identity verification that requires evidence of a user’s identity from two or more factors before admitting them to an account, application, or website. It’s far more difficult for hackers to crack MFA than is to crack single-factor authentication. Think of it like locking up your bike with two locks – it makes it far less appealing to a criminal who’s looking to steal a bike. Depending on the platform, the evidence a user must produce to verify they are an account’s true owner can include:
Have you enabled MFA?
Many online accounts offer MFA as an added layer of security. It is now common for accounts to prompt you to turn on MFA when you first sign up, such as the 2-step-verification method used when logging into online accounts after a period of inactivity. Often, however, MFA is disabled by default and requires the account holder to manually turn it on. You’ll normally find the option to enable and configure authentication tools in the application’s account settings.
Have you considered using an authenticator app?
Authenticator apps connect to accounts that support MFA and randomly generate secondary login codes. When logging into to an account a single use authentication code is sent to you through the app, making the process time sensitive and very difficult for scammers to crack. There’s a wide range of trusted authenticator apps available, most of which are free. Find out more about authenticator apps in this article by Tech Radar.
What are portable devices and removeable media?
What are the risks of using portable technology?
The same factors that make portable devices and removeable media so convenient also make them a cyber security risk. Here are some of the security risks associated with these devices:
How to use portable devices safely
Although convenient to use, portable devices and removable storage can hold lots of private information and sensitive data in one place, so don’t overlook their security. Remember these key take-aways to keep yourself protected:
Cyber security incidents at work can be difficult to spot. Decisive action may stop attempted attacks before they become full-scale disasters. Here are steps you can take to minimise the impact if you think you’ve been exposed to an online attack at work:
While cyber security measures continue to evolve and improve, one thing is certain; there will always be criminals out there trying to hack into accounts. Practicing smart security with all your devices is the best defence against the darks arts and sensitive information falling into the wrong hands.
Here are some key takeaways and remember, it’s not SAD to be safe!
Stay informed about the latest techniques and scams criminals are using.
Act quickly if you think you or your organisation have been exposed to criminal activity. The sooner you report an incident, the quicker it can be resolved and the less damage it will cause.
Do not act if something feels “off”. Criminals pray on unsuspecting users, so stay alert to potential threats and keep those trigger fingers under control.
The Digital Culture Network is here to support you and your organisation. Our Tech Champions can provide free 1-2-1 support to all arts and cultural organisations who are in receipt of, or eligible for, Arts Council England funding. If you need help or would like to chat with us about any of the advice we have covered above, please get in touch. Sign up to our newsletter below and follow us on Twitter @ace_dcn for the latest updates.
Beginner Read Digital Strategy
An effective digital strategy can be vital to your organisation’s success. Read on to understand the key considerations when developing yours.
Beginner Read Digital Marketing
Five recommendations to help improve your digital marketing performance.
Beginner Read Digital Strategy
Do you have a good understanding of which parts of your digital strategy are working? Our diagnostic will help you assess and improve your activities.
Intermediate Read Digital Strategy
Do you often find yourself juggling 10 different tasks at once? Do you find you are not doing things as well as you know you could? This article will help you to streamline your marketing and redirect focus towards feasible and sustainable goals.
Beginner Read Data Analytics and Insight Digital Marketing
Excel is arguably the most powerful software at sorting data into meaningful categories and the go-to tool for most marketers and data analysts, particularly when it comes to reporting. This article will introduce you to ten functions, formulas and shortcuts to try next time you are manipulating your metrics.
Beginner Read Digital Marketing Digital Strategy Social Media
Writing a landing page headline in 6 to 12 words is not as simple as it first appears but there is a straightforward process you can follow to move from a poor-performing headline, to one that performs. Read on to learn about the key steps you should consider following to optimise your landing page headlines.




